Users
This panel shows the list of all users currently existing into the system.
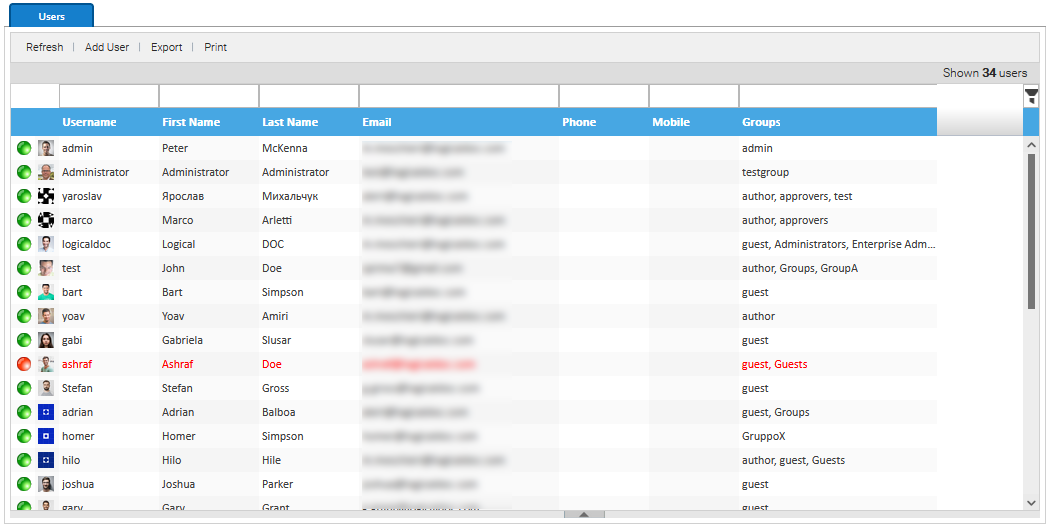
To add a new user, you have to click on Add User button and then fill all the required data:
- Username
- First Name
- Last Name
- Language
- Group
Each user can belong to one or more groups, the security policies are always expressed in relation to the groups and/or specific users.
There is also the Password expires option that allows to assign a time to live to the password. After the expiration days, when the user tries to access to the system, a warning message appears inviting him to change his password. The user must type his old password and then type a new one.
When you click the Save button (assuming all the required information have been correctly entered), a new user is created and added to the database. Then he receives a welcome e-mail containing the username and password created by the system. If you want to force a specific password, just right click and select Change password.
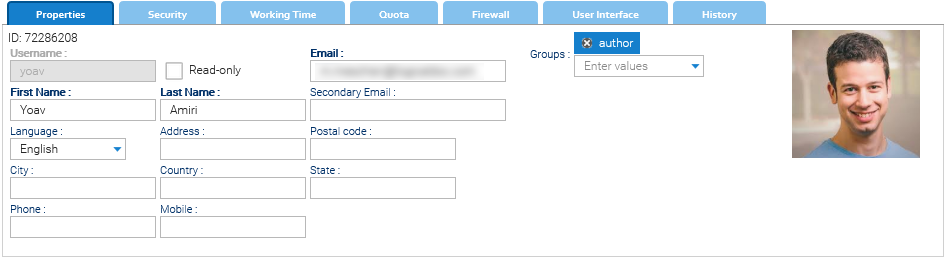
By selecting a user item, you can see all the user details under the list. Here you can edit the item's data.
Permissions inheritance
The security model implemented by the system allows you to express security policies for various permissions. These security policies are expressed in relation to groups and users, so each user inherits the access privileges assigned to all groups he belongs to
Avatar
LogicalDOC tries to use the Gravatar service to get an image representing the user, but you can change it an any time by right-clicking on the image and uploading your file.
Legal representative
Those users marked as Legal representative will be required to acknowledge changes in the legals like EULA, Support terms and conditions etc. Each time a new legal gets published, those users will be guided to read and confirm it before logging into the system.
Security
In this panel, there are various security aspects related to the user.
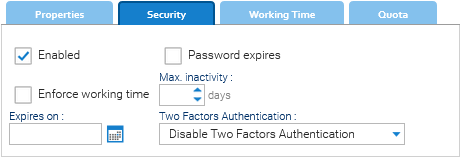
- Enabled: if not enabled, the user cannot enter the system
- Password expires: if the password of the user expires after a period
- Max. inactivity: optional maximum number of days since the last interaction, after which the user is marked as disabled
- Expires on: a date, after which the user is no more admitted to enter the system
- Two Factors Authentication: what two factors authentication must be implemented for this user
- Enforce working time: if the system must allow the user to login during his working time only (see the dedicated tab)
Working Time
For every user, you may define the working hours of each day in the week.
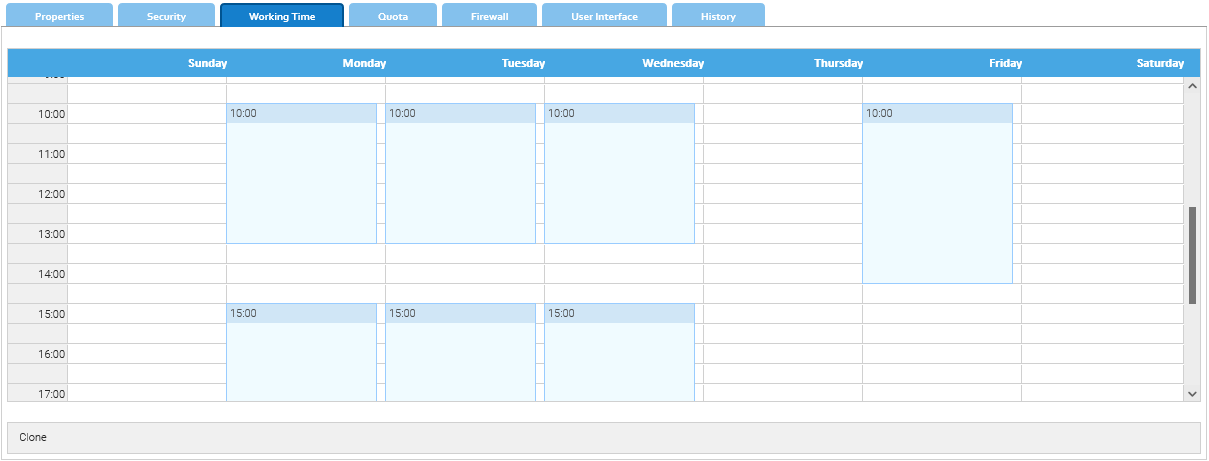
Just fill the grid like you do on a normal web calendar, for every block you can also give an optional label.
If you want to replicate the same working time for other users, just click on Clone.
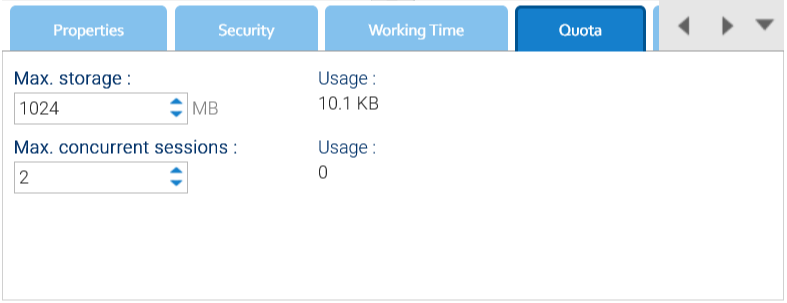
Quota
In this panel, you can define the user's quota.
Max storage: the maximum total size(MB) of the documents stored by the user
Max concurrent sessions: the maximum number of sessions the user can open at the same time
Read-only users
You can mark a user as read-only, if you do so the user will be automatically assigned to the guest group.
A read only user acts like a regular user but in spite of the security policies you may configure, he will not able to:
- Create / edit / delete / move files
- Create / edit / delete / move folders
In few words, this kind of users can only consult the platform but cannot fully interact with it.


