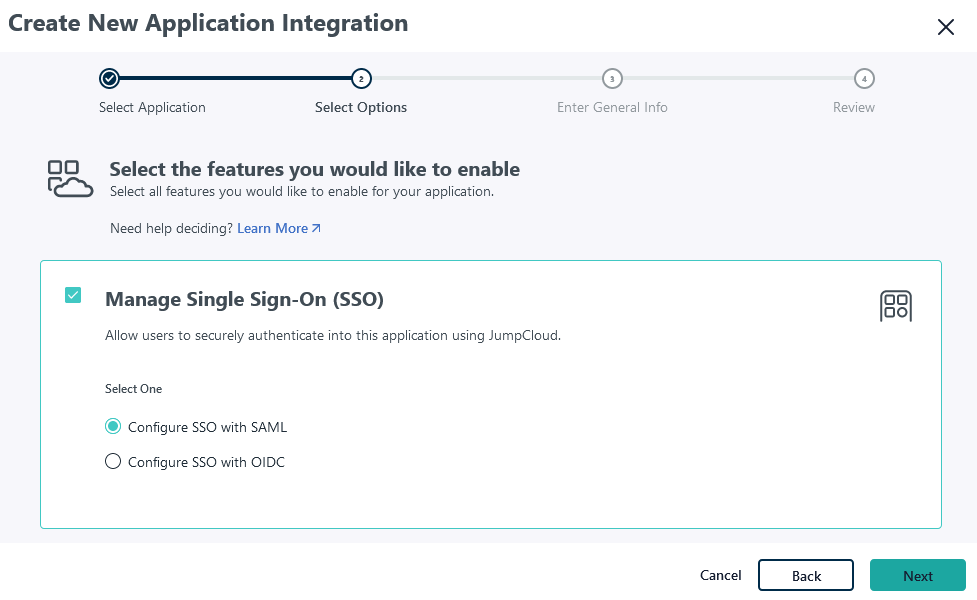
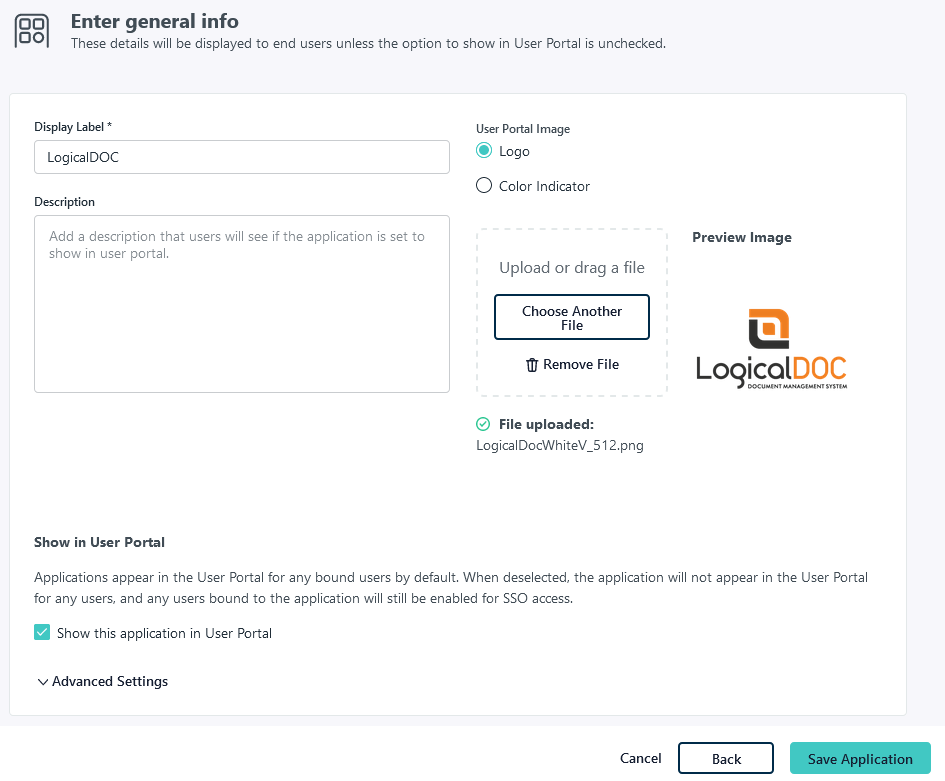
SAML Single Sign-On
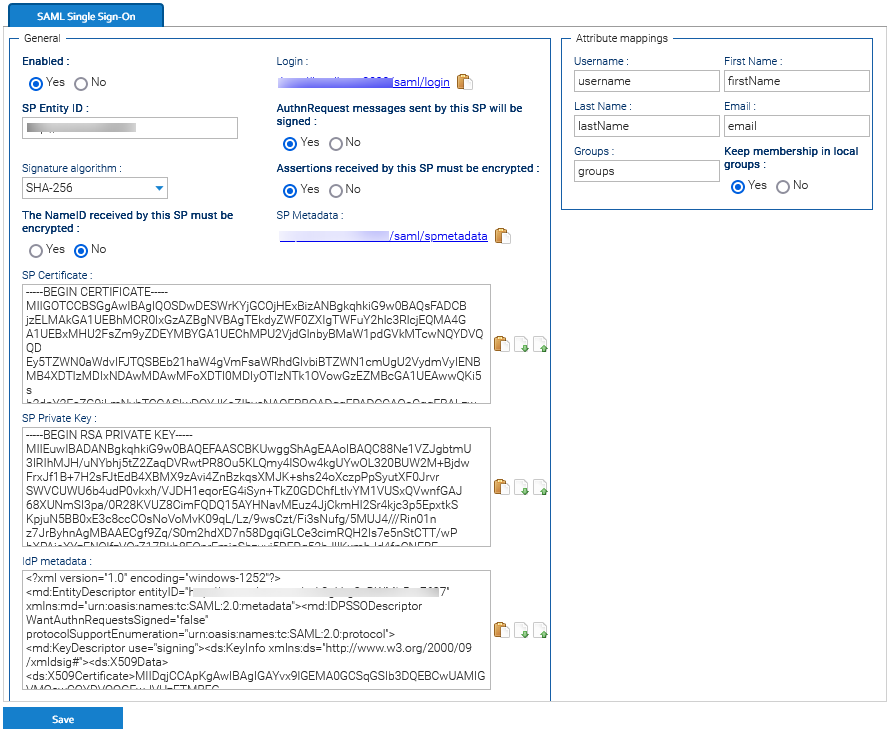
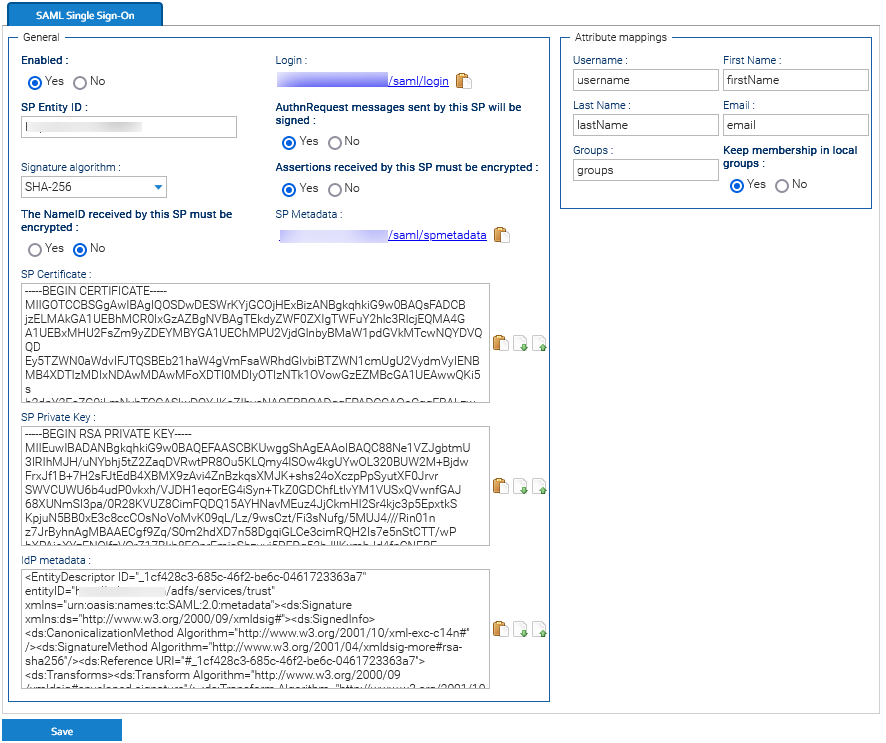
Single Sign-On (SSO) is a way for users to log into multiple applications with a single user ID and password without having to re-enter their credentials. The SAML standard allows identity providers to pass credentials to service providers. LogicalDOC can be configured to act as a SAML 2.0 Service Provider (SP).
Security Assertion Markup Language (SAML) is an open standard that allows identity providers (IdP), like Okta, to pass authorization credentials to service providers (SP), like LogicalDOC.
In simpler terms, it means you can use one set of credentials to log in to many different sites. With a SAML identity provider account, you can log in to LogicalDOC and other sites securely with the same account.
The main benefit is that it helps administrators centralize user management by controlling which sites users have access to with their SAML identity provider credentials.
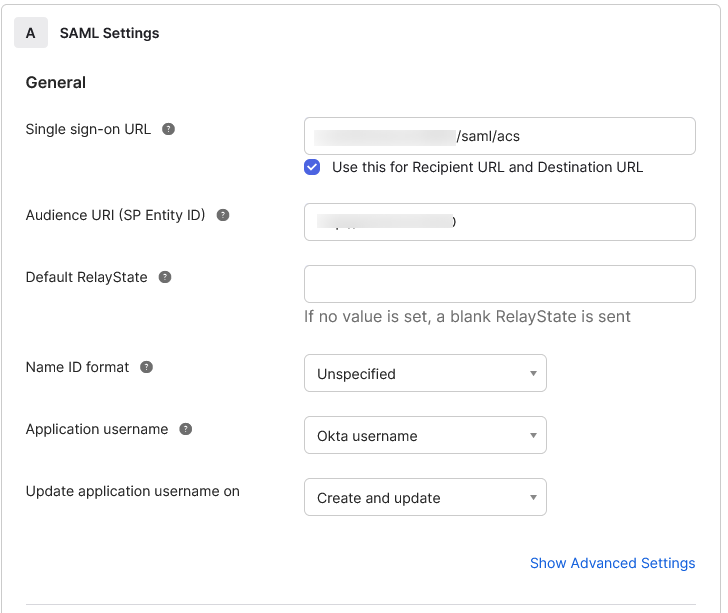
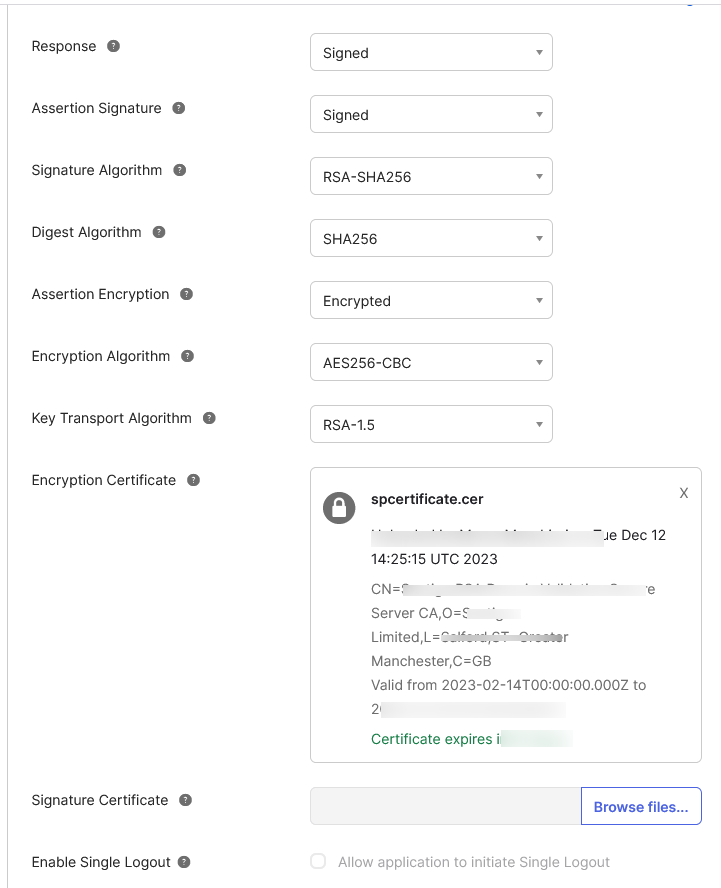
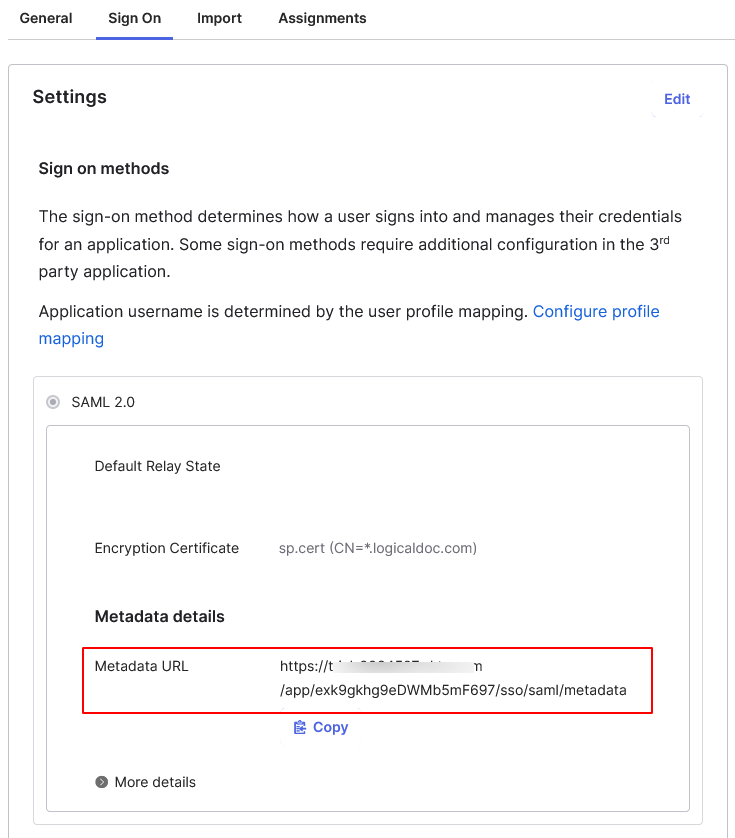
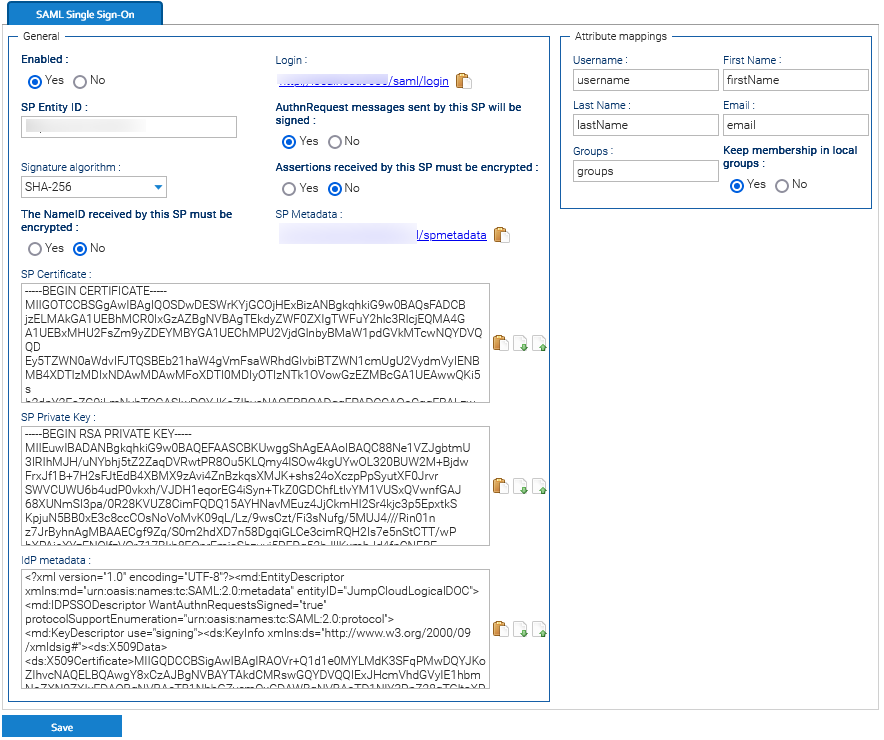
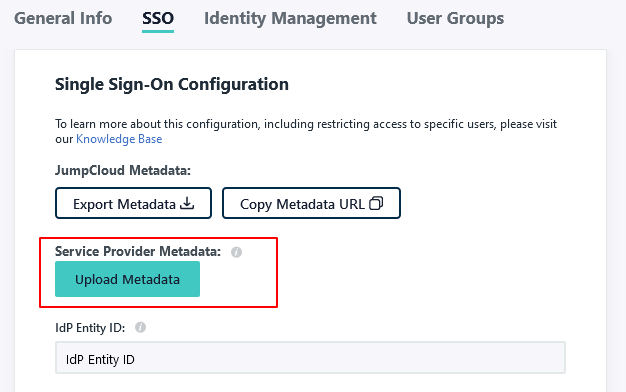
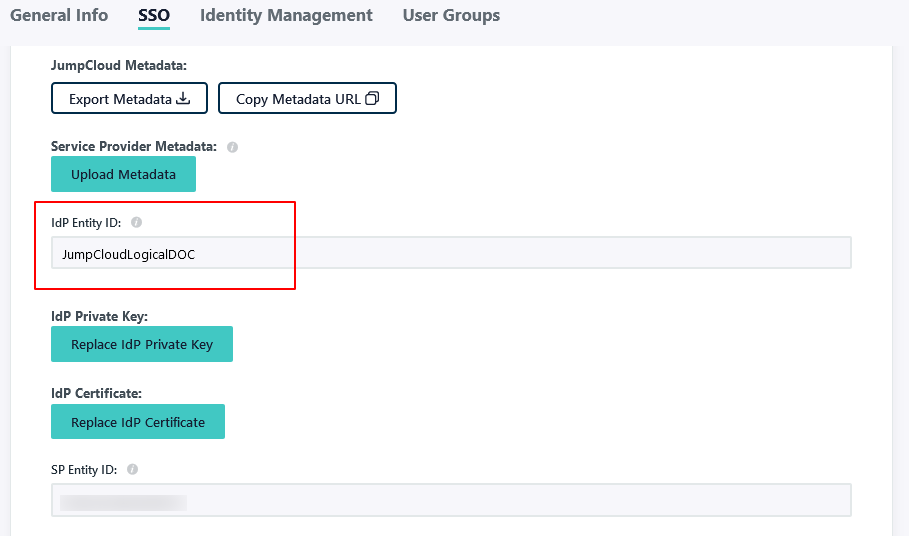
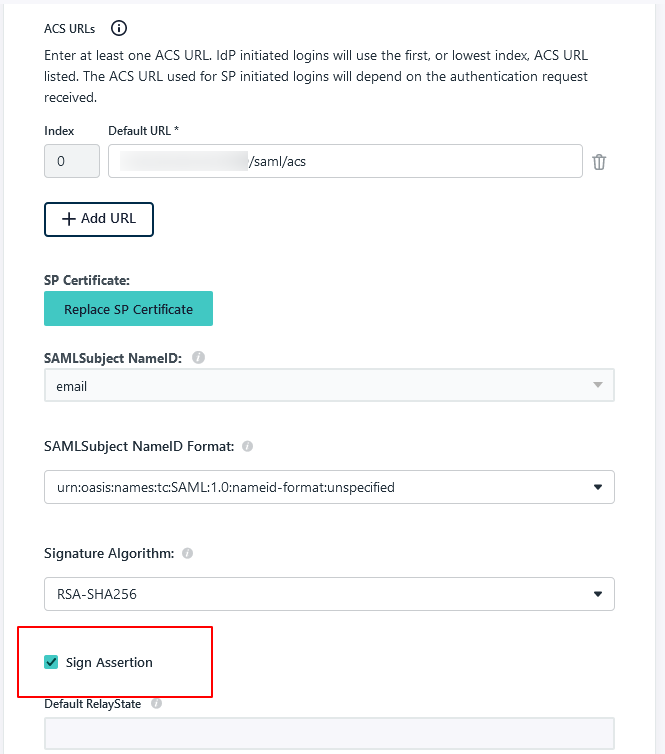
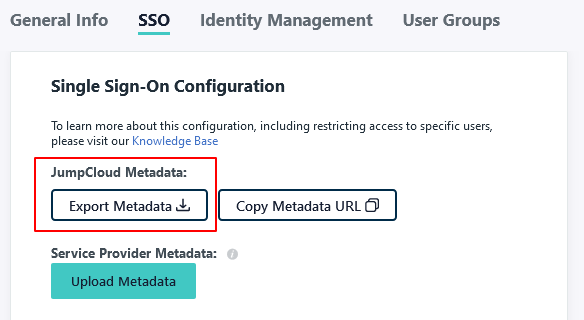
LogicalDOC supports using a single metadata file to retrieve configuration information for the Identity Provider. The IdP metadata XML file contains the IdP certificate, the entity ID end the redirect URL.
The SAML Single sign-on integration offers the following benefits:
- Single Sign-On. Users can log in to LogicalDOC with their SAML credentials.
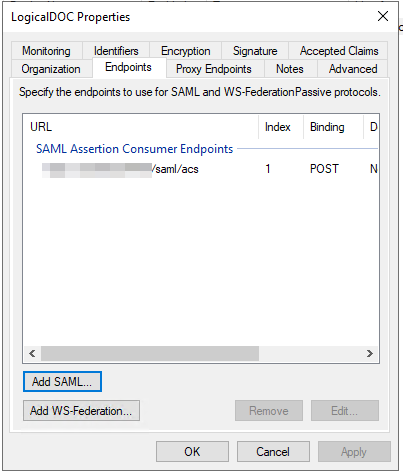
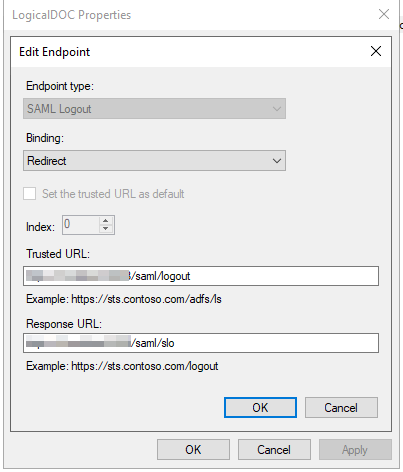
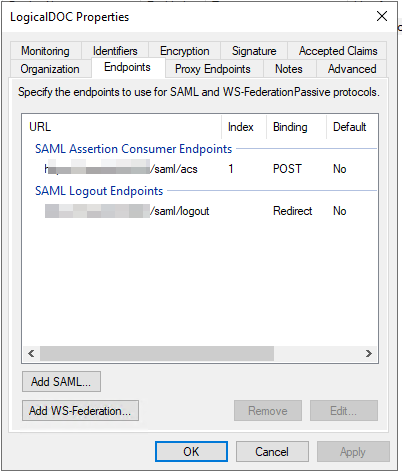
- Single Logout (SLO). As an option, a user signing out from LogicalDOC will be signed out from all the other applications that he was signed in using the same credentials.
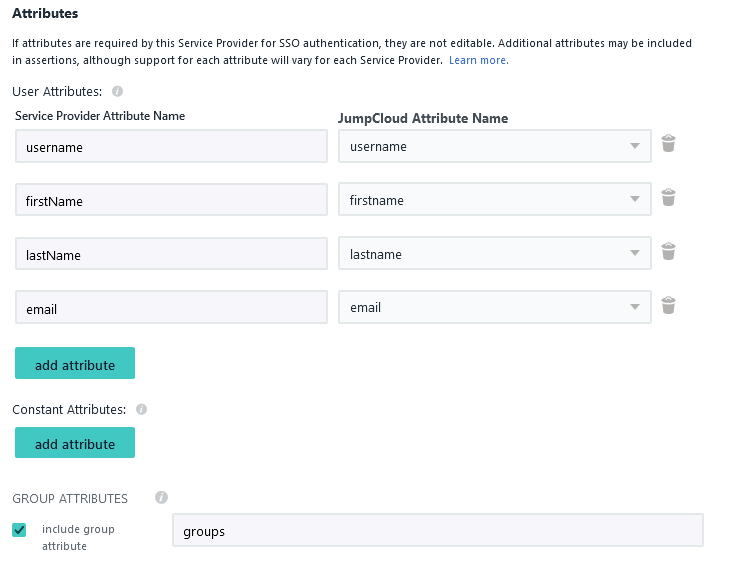
- Centralized identity management. LogicalDOC accounts automatically pull user attributes from SAML upon login, such as full name, email, and username.
- Automatic account provisioning. LogicalDOC user accounts are automatically created the first time a user signs in with their SAML credentials.
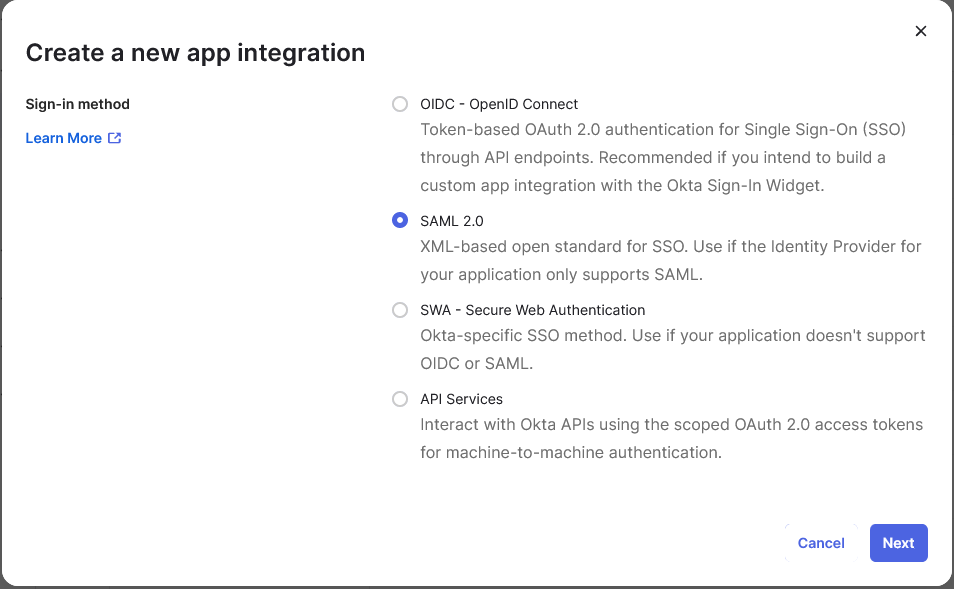
At the time of writing LogicalDOC was tested with Okta, JumpCloud and Microsoft Ads as the identity providers (IDPs), please see links below for more details on how to configure SAML with these providers.
In addition to these identity providers, you can also configure SAML for a custom IdP. It is important that you test new versions of LogicalDOC in a staging environment to confirm it will work with your identity provider.
Info
Even if you enable the Single Sign-On, the standard login page continues to be available and works as usual.
Validation
You may optionally provide an automation procedure invoked any time a user is about to be authenticated through the SAML to decide if it must be authenticated or not, or to perform further elaborations on the user itself. The automation procedure will receive the variable samlUser, use the boolean flag samlUser.valid to mark the user as authorized or not.
Dictionary available for the Automation in this context
Read the Automation manual for more information.