Security Settings
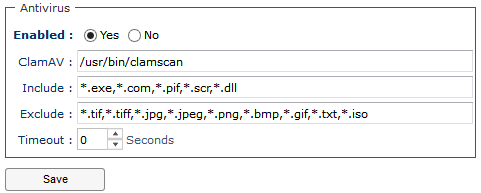
Into the Security panel, you fins some general settings related to the security of the system.
Security
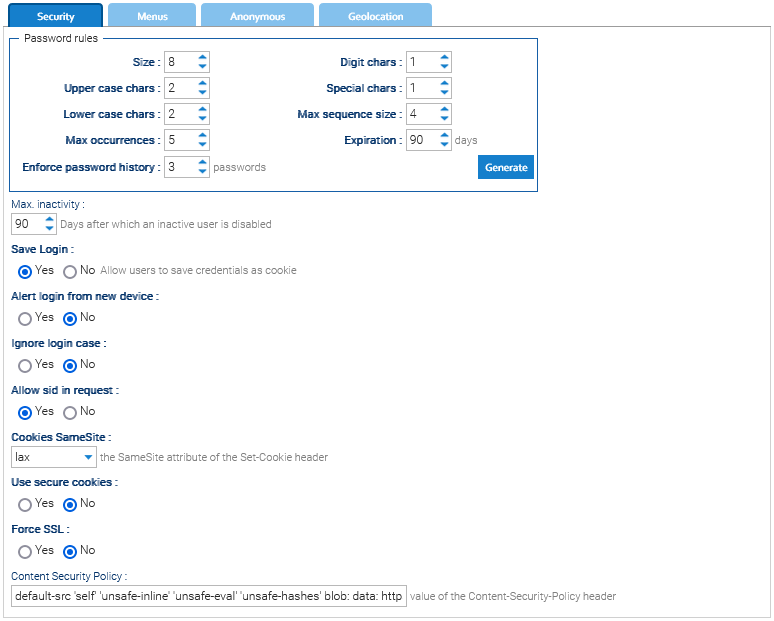
Password rules
You may define a set of rules to enforce a minimum quality of the password for the users. Use the Generate button to generate a sample password compliant with all the configured rules.
Size: The character size of the password (represents the minimum character size of the password)
Upper case chars: Minimum number of uppercase characters
Lower case chars: Minimum number of lowercase characters
Max occurrences: Maximum number of occurrences of the same character
Enforce password history: Prevents the reuse of a password already used N times before
Digit chars: Minimum number of digits
Special chars: Minimum number of special characters
Max sequence size: Maximum number of sequences (these are sequences of characters of the same type, e.g., 1234, abcd, GHIJK)
If the sequence is longer than the maximum number, it prevents the password from being set.
The comparison operator is <=, so the number of sequences must be <= the set number.
E.g., with 4, the sequence 56789 is not accepted, while 56689 is.
The same applies to the sequence GHIJK, while GHIJT is accepted.
Note: This parameter is case-insensitive.
Password expiration: duration of the password before being asked to change it
Enforce password history: number of old passwords remembered by the system for each user in order to prevent their re-usage
Other security settings
Max. inactivity: If a user does not have any interaction with the system within this number of days, it will be automatically disabled.
Save Login: if the users have the option to store their credentials in the browser
Alert login from new device: Alerts the user when logging in from a device not yet encountered
Ignore login case: if LogicalDOC must ignore the case of the username to authenticate the users
Allow sid in request: permits the sid attribute in the request in order to pass the session identifier. Activate this option only if really needed because it may compromise the security.
Cookies SameSite: determines when cookies are included in requests
Use secure cookies: enables the cookies only when using the HTTPS protocol
Force SSL: if active, LogicalDOC will redirect all HTTP requests to the HTTPS secure protocol (read this how-to for installing your Certificate)
Content Security Policy: the content to put in the HTTP response header Content-Security-Policy.
Check at login: checks the password compliance at login and if it does not comply, the user gets forced to change it.
Anonymous
By activating this option, you can grant access to the system by anonymous users without passing through the login page and the normal authorization chain.
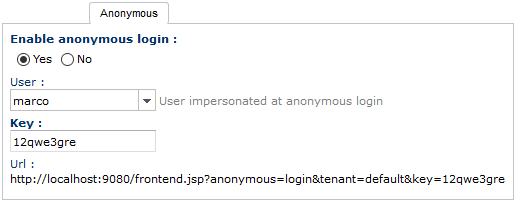
When the option is enabled you can distribute the special URL as shown above, to people not registered in the system. Anyone accesses to that URL will be automatic logged in as he was the user selected in the User parameter.
The anonymous visitor can do inside the repository whatever thing that the assigned User can do on the basis of the security policies that you granted him. Please note that part of the anonymous URL is regulated by the Key parameter, so change it in case you need to invalidate already distributed URLs.
Use with care
Please enable this option just in cases where you really need it, and make sure to assign a user with limited access to your repository
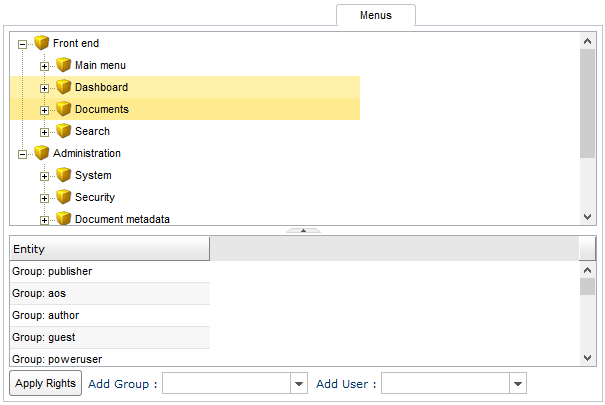
Menus
In this panel, you can determine which entities (users and groups) can access a menu. After selecting a menu item, to add new security entities use Add Group and Add User list boxes, to drop an element right-click on the name and press Delete. If you want to make your changes persistent, you have to press the Apply Rights button.
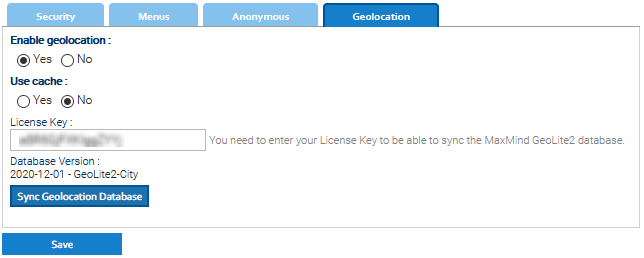
Geolocation
LogicalDOC is able to geolocalize all the incoming requests, and this gives you the opportunity to track where your users are coming from. We use the GeoLite database, so you have to input your MaxMind License Key. You get your free license key by subscribing to GeoLite2 here: https://www.maxmind.com/en/geolite2/signup
It is important to maintain updated the GeoLite database, so from time to time click on Sync Geolocation Database
Precision
The geolocalization is possible only when the request comes from a public IP and in any case the precision totally relies on the used GeoLite database, so it is important to maintain it as updated as possible.