The application is able to handle users authentication interacting with external systems in addition to the standard authentication. We can authenticate your users against ActiveDirectory and LDAP systems.
Please enter the section Administration > Security > External Authentication
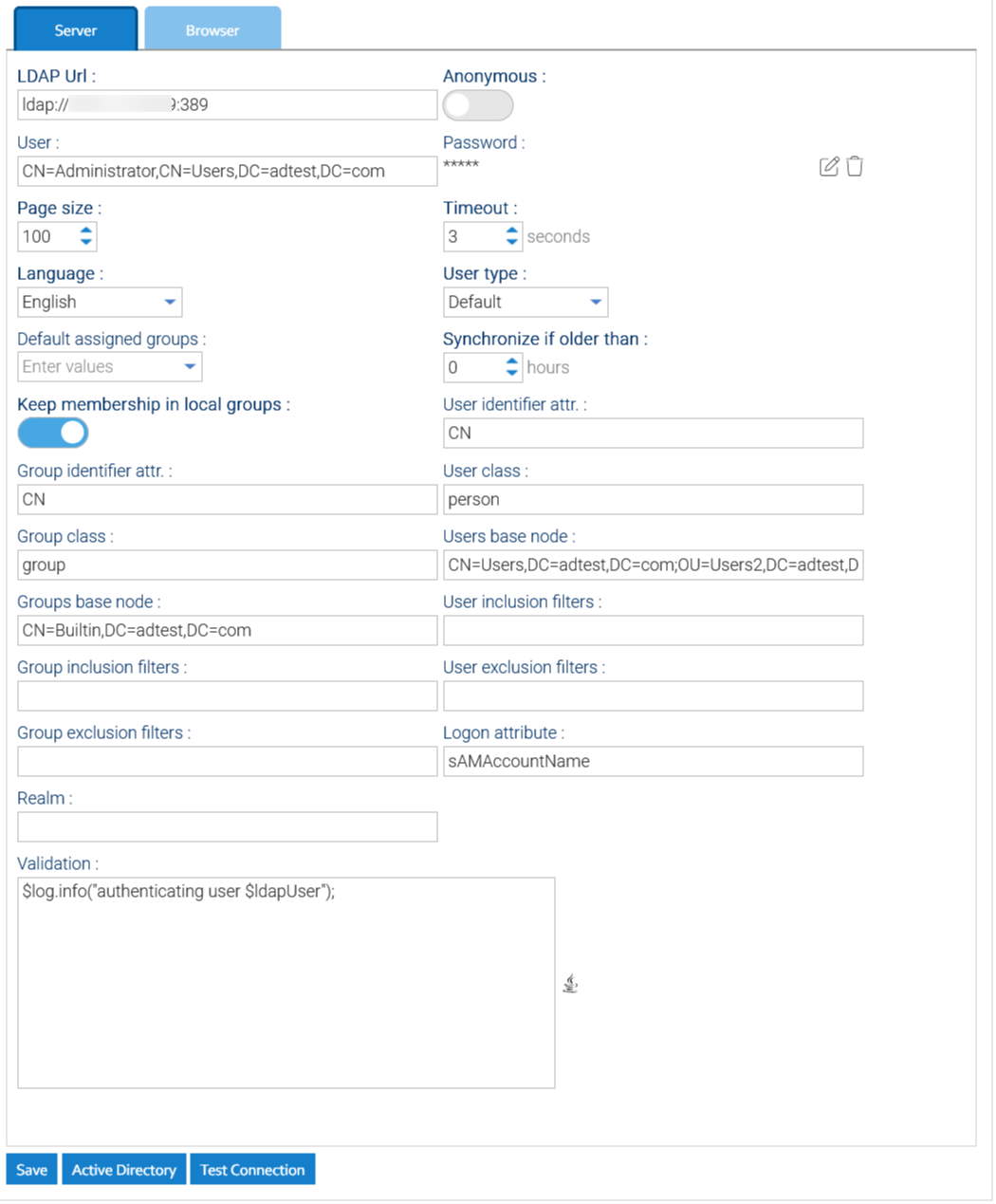
Here you can configure the connection to a set of LDAP and/or AD servers:
- URL: complete connection URL to the external authentication server including port number (for ActiveDirectory it is 389)
- Username: username of a user that can perform searches inside your LDAP/ActiveDirectory (for ActiveDirectory you have to put the canonical name of the user)
- Password: password to connect
- Users base node: canonical name of the root node where the users are located (you can define more nodes separated by semicolon ';')
- Groups base node: canonical name of the root node where the groups are located (you can define more nodes separated by semicolon ';')
- User Inclusion / Exclusion filters: comma separated lists of expressions to restrict the usernames to allow, eg: inclusion: usr*,user* exclusion: sysem*,Administrator,Sysadmin
- Group Inclusion / Exclusion filters: comma separated lists of expressions to restrict the group names to allow, eg: inclusion: grp*,group*,staff exclusion: Admin*,Power*
- Timeout: max time to wait an answer from the authentication server
- Synchronize if older than: number of hours after which the profile of local user is updated with the current data from the directory (0 means always synchronize, -1 means never synchronize)
- Keep membership in local groups: If enabled, the memberships you define in LogicalDOC will be retained otherwise they will be overwritten by those specified in the LDAP or AD server
- Validation: an automation procedure invoked any time a user is about to be authenticated through the LDAP to decide if it must be authenticated or not, or to perform further elaborations on the user itself. The automation procedure will receive the variable ldapUser, use the boolean flag ldapUser.valid to mark the user as authorized or not. Se more about the automation here
To check if the connection parameters are correct, just click on Test Connection.
Once you have connected the external directory, click on Save to make persistent your changes.
On the fly authentication
The next time a user tries to log into LogicalDOC, he will be authenticated against your LDAP/ActiveDirectory first and if the process completes successfully, the user's profile(but not the password) is also automatically imported in LogicalDOC.
Manually import users
From time to time you may want to manually import a new user from the LDAP/ActiveDirectory, in this case open the Browser tab and here below click on Search to fiind all the users located at any level below the configured base node.
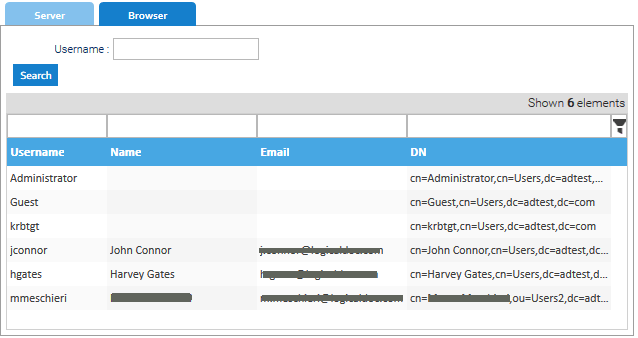
Right-click on the user you want to import and select Import. When the user is imported, the groups he belongs to(and that fall below the groups base node you configured before) are imported as welll.
Security policies
When the user is imported the first time, you will have to grant him and/or his groups the permissions in LogicalDOC. By default, the imported user has the same permissions granted to the guest group.
Security implications
LogicalDOC needs to retrieve the profile information of the user from LDAP(email, phone etc.) so it requires the serialization. Please use trusted LDAP servers only, and in any case to connect to it with read-only permission credentialsActive Directory
Click on Active Directory to launch a small wizard that applies some standard parameters suitable for connecting to an AD domain server.



